Wireguard notes
Wireguard notes
Peer’s Configuration File
An example of a peer configuration file:
[Interface]
Address = 10.13.13.2
PrivateKey = base64_encoded_peer_private_key
ListenPort = 51820
DNS = 10.13.13.1
[Peer]
PublicKey = base65_encoded_peer_public_key
Endpoint = mywireguardserver.com:51820
AllowedIPs = 0.0.0.0/0
AllowedIPs: This field instructs the peer to only send traffic over the VPN if the destination has an IP in that range. If you want to send all traffic over the VPN use 0.0.0.0/0 for IPv4 and/or ::/0 for IPv6. If instead you only want to use the VPN for some local IPs for example you can enter the range here (for example use 10.13.13.0/24)
Display QR code
Once the peers (clients) are configured running the following command to a specific peer config file (in this example ~/docker-fleet/wireguard/config/peer1/peer1.conf) will display a QR code for easier setup on some devices like phones.
qrencode -t ansiutf8 < ~/docker-fleet/wireguard/config/peer1/peer1.conf
Configure a client on KDE
On system setting –> Connections, click on Add new connection and Import VPN connection:
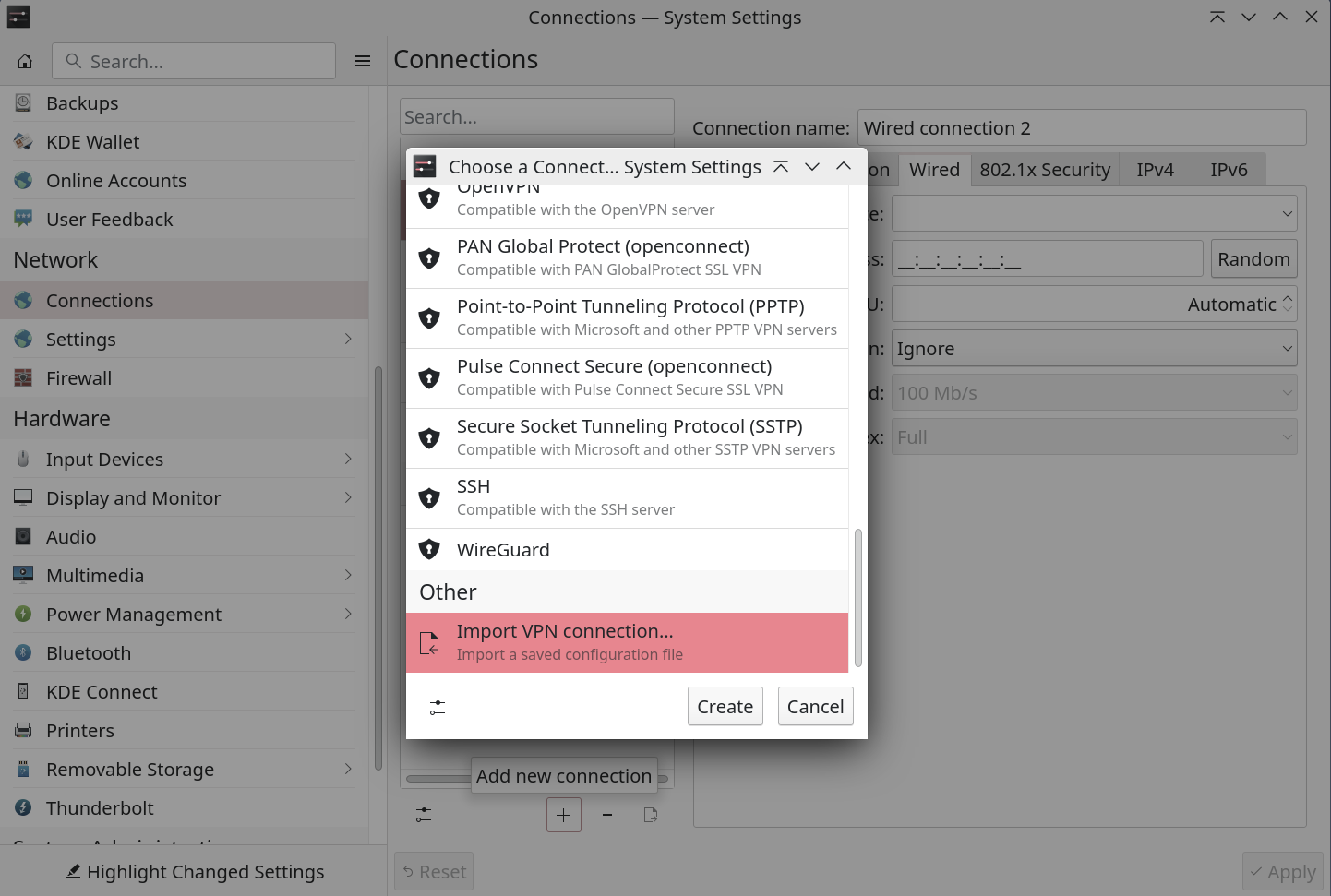
Select you peer.conf file and the Wireguard connection will get created
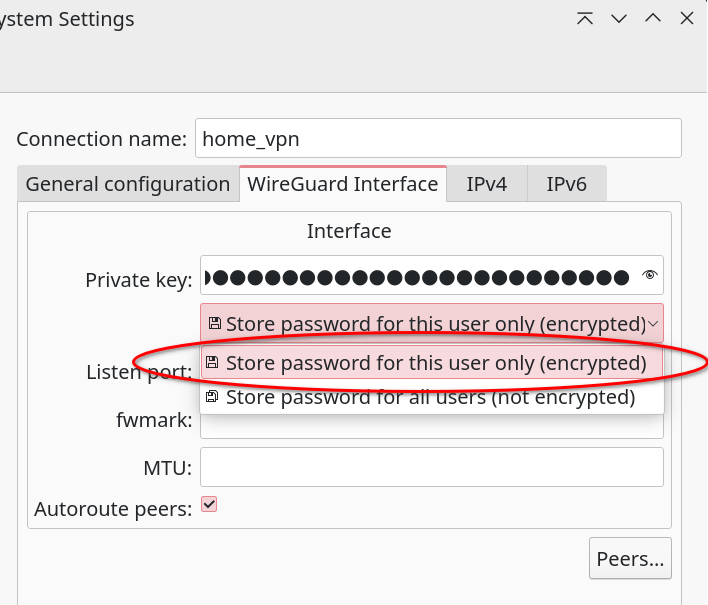
By default this will store the private key uncrencrypted and available for all users. I prefer to change that to Store password for this user only (encrypted).